Ransomware Prevention Best Practices 2026: A Complete Guide
As of 2025, the ransomware plague is spreading uncontrollably and getting deadlier with no signs of stopping. A few notable recent attacks include the Casio breach by Underground ransomware, the PowerSchool attack, and various healthcare and education attacks by Rhysida and RansomHub. But of course, there’s more:
By 2031, a new ransomware attack is projected to occur every 2 seconds. (Cybersecurity Ventures)
January 2025 kicked off with a record-breaking 92 disclosed ransomware attacks, a 21% increase over last year and the highest recorded since tracking began in 2020. (BlackFog, 2025)
It is predicted that cybercrime will cost the world $10.5 trillion a year from 2025 (Spacelift, 2025)
We believe you understand how bad it is, which is why you’re on this page.
The table of contents below helps you navigate to the part you want to learn about first. The important points in each section are in bold if you’re short on reading time.
TABLE OF CONTENTS
Defining Ransomware and Its Top Variants
Best Practice #1: Include Ransomware Prevention in Your Business Strategy
Best Practice #2: Not Falling for the Biggest Misconception About Preventing Ransomware
Best Practice #3: Understanding the Stages of a Ransomware Attack
Best Practice #4: Using a Layered Security Approach to Prevent Ransomware
Best Practice #5: Being Prepared for a Successful Ransomware Attack
No Cost, Big Protection.
Download Mamori Freemium and begin securing your jump servers with Mamori.io’s free, easy-to-use solution.
Defining Ransomware and Its Top Variants
Ransomware is a type of malicious software designed to deny access to a computer system or files, typically by encrypting them, until a ransom is paid, usually in the form of cryptocurrency. Today, ransomware attacks are largely carried out by “ransomware gangs”, such as BlackCat, Lockbit, and Scattered Spider, where they threaten to leak the compromised data if the victim doesn’t pay the ransom.
Although there are more than 10,000+ ransomware variants as of 2022, below are the top ones used:
WannaCry: It exploits a vulnerability in Microsoft Windows SMB (Server Message Block) protocol to spread across networks.
NotPetya (ExPetr): It propagates through the same SMB vulnerability as WannaCry and also utilized other methods, such as compromised software updates.
Locky: Spreads through malicious email attachments, often in the form of Microsoft Office documents containing macros.
CryptoLocker: Typically spreads through malicious email attachments or compromised websites.
Ryuk: Often infiltrates networks through phishing emails or by exploiting vulnerabilities in Remote Desktop Protocol (RDP) connections.
Sodinokibi (REvil): A ransomware-as-a-service (RaaS) that spreads through various methods, including phishing emails, exploit kits, and compromised Remote Desktop Protocol (RDP) connections.
Maze: It spreads through phishing emails, exploit kits, and remote desktop services.
From the above, you can already see a few commonalities on how ransomware gains entry and spreads. In the following sections, you’ll learn the stages of a ransomware attack and how to stop these attacks.
Best Practice #1: Include Ransomware Prevention in Your Business Strategy
Why is it important to include ransomware prevention in your business strategy? The biggest reason is that “it is bad for business”. To be more precise, a ransomware attack can:
Cause financial loss – Whether in the form of paying the ransom, or in the form of disrupting your business operations where you lose revenue by the minute.
Disrupt operations and business continuity – Your business cannot operate when you cannot access mission critical data
Legal liabilities – Ransomware gangs may threaten to publicize sensitive data, and you may be held liable for not properly protecting those data.
Reputation damage – Most ransomware attacks make it to the news, which harms customer trust and damages your brand.
As such, here are some points to help you with your ransomware protection strategy:
Revisit your Business Continuity Plan and Disaster Recovery Plan, including your backup strategy, to include ransomware prevention and ransomware recovery.
Get buy-in from business and IT leaders on the consequences of a ransomware attack and the level of investment needed to prevent ransomware attacks.
The prevention strategy should include people, process and technology. For people, it includes employee awareness and training on phishing attacks and malicious email attachments. Process includes workflows, such as creating accounts with excess privileges or accounts for short-term contractors. Technology includes the solutions implemented at each layer when accessing your data.
This article will teach you how you can realize your ransomware prevention strategy using a layered security approach and will briefly touch on the people and process. But first, let’s address the top misconception
Best Practice #2: Not Falling for the Biggest Misconception About Preventing Ransomware
The biggest misconception is that ransomware attacks applications. Ransomware attacks do NOT target applications. This means securing application access using two factor authentication (2FA) does nothing to prevent a ransomware attack.
Instead, ransomware hackers are going after your files and data, and that includes documents, database files, or table data in your database. To get to your documents, they need access to your network shared drives. To get to your database files, they need operating system access via SSH or RDP (more on this below). To get to your table data, they need access to your database.
Thus, another best practice is NOT to use application security to defend against ransomware. The applications have no data. Data is inside the database that these applications have access to.
To get to those data, a ransomware attack’s first step is to gain an entry point.
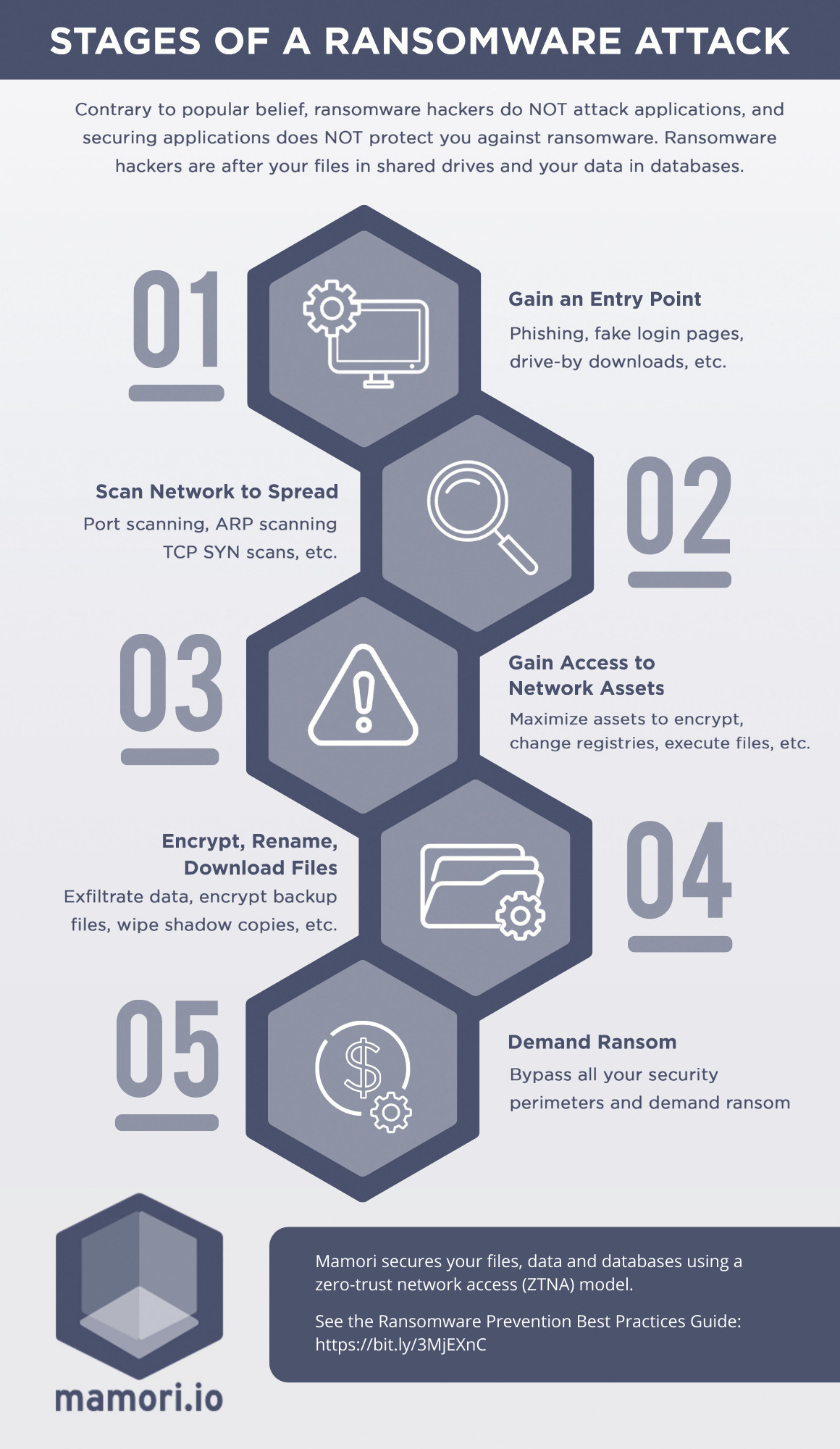
Best Practice #3: Understanding the Stages of a Ransomware Attack
Once you understand the stages of a ransomware attack, you’ll better understand on the people, process and technology that is needed to prevent ransomware attack. Below are the 4 stages of a ransomware attack.
Stage 1: Endpoint – Gaining an Entry Point
Ransomware’s goal is to encrypt ALL your organization’s files and data and/or steal your data. But to do so, hackers need an entry-point. The most common entry point is through an employee and his device. Tactics to do so include:
Phishing emails, social media, or chat apps: Emails appearing to be legitimate but contains malicious attachments or links intended to steal your credentials.
Malicious websites, fake login pages, or file-sharing: Visiting these sites can trigger download and installation of ransomware onto a device (Drive-by Downloads). Other sites may mask as a legitimate login page to steal credentials.
Exploit kits: Exploits vulnerabilities of the victim’s browser-based applications and silently installs malware on the target computer, usually delivered using malicious websites.
Remote Desktop Protocols (RDP) or Virtual Private Network (VPN) Attacks: Exploits weak or default credentials and logging in as a user or administrator. For instance, RDP connection is through port 3389 by default, and cybercriminals leverage this by using port-scanners to scour the web for exposed ports.
Malicious Software Updates: Disguises the malware as a legitimate software update so the user downloads and installs it unknowingly.
USB or Removable Drives: Infects a device when a user inserts the USB or removable drive into their device. This method is less common nowadays.
Stage 2: Network – Scan Network to Spread
Ransomware needs to spread across the company’s network to maximize damage, which increases their chances of getting their ransom demand paid. To do so, their next step is to scan the organization’s network to spread. Their mission at this stage is to do reconnaissance. They need to learn more about the organization’s network, nodes, and applications surrounding the compromised device. Common methods deployed include port scanning, ARP scanning, or vertical TCP SYN scans.
Stage 3: Escalate Privileges – Gain Access to Network Assets
At this stage, cybercriminals have knowledge of the organization’s network. Their next step is to gain further access into the network and other machines to maximize the assets they can encrypt.
This stage is when they begin harvesting other credentials, such as an IT manager, to gain administrator privilege to the organization’s network. At the same time, they will attempt to change registries, execute specific files or programs on the network, and breach the security console to disable or bypass the organization’s security software. At this stage, the attack becomes highly tailored and specific based on what they discovered about the organization’s network from searching and scanning. The goal is access, encrypt and download all company files and backups in order to carry out a successful attack.
Stage 4: Access Resources & Data – Encrypt, Rename and Download Files
When cybercriminals have access to mission-critical files, they begin encrypting them and replacing the originals with the encrypted files. Most ransomware variants do so without taking down the IT infrastructure. Backup files that they have access to will also be encrypted. Files will be renamed, and shadow copies of files will be wiped to hamper file recovery without decryption.
At the same time, they usually conduct data exfiltration and theft by downloading critical or sensitive files from your network. Cybercriminals will threaten to release those sensitive data to the public to extort the organization to pay the ransom.
Stage 5: Demand Ransom and Extort
At this stage, the ransomware has bypassed all your security parameters. Cybercriminals will demand a ransom payment once an organization’s critical files and backups are encrypted. In cases where they weren’t able to locate or encrypt the backup, they will threaten with other means to demand ransom, such as releasing sensitive information on the web.
Best Practice #4: Using a Layered Security Approach to Prevent Ransomware
As mentioned above, a ransomware hacker has to go through stages to finally get to their final prize – your data. To prevent them from succeeding, the best practice is to use a layered security approach that is capable of stopping them at each stage.
Layer 1: Securing Endpoint and People – Blocking Ransomware Hackers from Gaining an Entry Point
SPAM FILTERS
Emails are the number one tool for ransomware to gain an entry point. An effective spam filter can prevent 99% of malicious emails from ever reaching an employee’s email inbox.
However, most spam filters use database to check on the sender’s IP address and domain reputation, which depends on the bounce rate of their email campaigns and whether someone reported those emails as spam. Thus, don’t be surprised when malicious emails pass spam filters.
There is a newer solution namely DMARC (Domain-based Message Authentication, Reporting and Conformance) an email authentication system that reduces your organization’s domains from spoofing, phishing and other attacks. While this is more effective, to configure and use this solution is not simple.
Hackers have now moved on to use many other means to do phishing, Facebook, Linkedin any social media, and any messaging/chat/SMS facility are now prone to be used as a phishing tool.
EMPLOYEE EDUCATION
Even when malicious phishing emails go through, an employee trained to identify phishing attempts can still prevent ransomware from getting a foothold. This training includes identifying the following:
Email attachments: Malicious emails pretending to be legit may include attachments such as invoice, proposal, or other important business topics.
Website links: These links can include fake login pages replicated to steal credentials and infected webpages that has drive-by-downloads.
Sender name and domain: Cybercriminals who know the names of employees or management may use those names to send the email. Other times, when they’ve gained access to certain domains, they may use those domains to send notices from legal department, claiming that you infringed on their rights. This method is known as social engineering.
Although employee education is one of the best lines of defense against ransomware, employees can get careless or accidentally visit a website with a drive-by-download.
In addition, employees should be trained to report phishing attempts immediately, strengthen their passwords (including where and how they store their passwords), and only download files from verified and known sources.
Even so, employees can get careless or accidentally visit a website with a drive-by-download. When this happens, you next layer’s security will be put to the test.
ENPOINT PROTECTION
A good endpoint protection helps stop malicious files from executing and infecting devices, such as drive-by-downloads or malicious email attachments. Some endpoint protection can even block file encryption and interrupt command-and-control (C&C) communication – a medium of communication for attackers to execute commands on the infected device.
The problem, however, is that most endpoint protection protects against known attacks and doesn’t protect the IT network and files from encryption. Similar to spam filters, the protection solution uses a database of what is known out there (such as URL reputation for drive-by-downloads), so newer attacks can still bypass this protection. Even if the solution’s database is up-to-date, the employee’s device protection software needs to be updated too.
VULNERABILITY SCANNER AND PATCH
This method scans and identifies all endpoints within a network where cybercriminals can potentially gain access to. It first discovers all the devices connected to the network. Then, it scans each endpoint device in order to compile a software inventory. The scanned results will list all the software versions in each device and notify the administrator of any outdated software or entry points in each endpoint that can be exploited by cybercriminals. Then, it is the administrator’s responsibility to patch the outdated versions.
Layer 2: Securing Perimeter and Network – Blocking Ransomware Hackers from Network Access
ZERO TRUST NETWORK ACCESS (ZTNA) WITH 2FA
This secures access to your network using the Zero Trust concept. A typical ZTNA solution has network access controls that can be limited by Two-Factor Authentication (2FA), device registry, IP addresses, netmask, or a combination of both IP/netmask while using Single Sign-On (SSO).
See also: See what Mamori.io’s free ZTNA solution can do for you.
SECURING REMOTE ACCESS
Virtual Private Network (VPN) or Remote Desktop Protocol (RDP) for employee remote access is another entry point for ransomware. The minimum level of security employed here is either using two factor authentication (2FA) or restrict access by IP address.
If you use Mamori.io, then all remote access is secured by identity and role-based IP and Port access controls. See also: Are Corporate VPNs Secure?
PENETRATION TESTING
This method searches for vulnerabilities in an organization’s systems and network by simulating a real-life cyber-attack on your network. The goal is to find entry-points into the system and identify where the weakest points are so organizations can properly secure their network. This practice is best performed by third-party experts familiar with the latest methods used by cybercriminals. Penetration testing should be conducted at least once a year to uncover network weaknesses, outdated security policies, insecure system settings, bad passwords, software bugs, configuration errors and more.
NETWORK FIREWALL
A network firewall provides many security features to help prevent ransomware. It can secure remote access, such as VPN or RDP, as mentioned earlier. It can eliminate non-essential open ports and secure essential ports. It can create a DMZ for web attachments and traffic so files can be properly analyzed before entering the network. It can create network traffic policies and stop the ransomware from contacting the cybercriminal on the internet.
However, managing firewall policies can be tedious, and many IT managers tend to forget the vast amount of policies created, not to mention if the role of managing these policies change hands. Thus, the better and easier approach is using Zero Trust Network Access (ZTNA).
NETWORK, TRAFFIC AND PROCESS MONITORING
Network monitoring should monitor for signs of infection or access. Assuming the ransomware has full network access, network monitoring should be able to detect unexpected edits in windows registry on servers and devices, edits to registry keys. It should also detect unusual internal and external traffic or bandwidth activity (downloads). In addition, network monitoring should also identify whether any new or unfamiliar processes and code are being executed, including file modifications so they can bypass security software or other security layers.
MICROSEGMENTATION
Ransomware loves an open network, and micro segmenting networks will make it much harder for ransomware to spread. Micro segmentation divides up an organization’s network into smaller networks, which greatly reduces the attack surface of ransomware. One practice is to segment a network for third party vendors or the less-trusted, more vulnerable parts of the network. However, there is no best way to segment a network because each organization have unique communication flows. Ultimately, protecting networks from unauthorized internal and external access is one of the most important elements of network micro segmentation.
See also: Microsegmentation best practices.
Image: How Mamori M4IP safeguards you from network penetration attacks or unauthorized insider access.
Layer 3: Securing Access to Application, Infrastructure, and Data – Blocking Ransomware Hackers from Data Access
DATABASE ACTIVITY MONITORING (DAM)
Database Activity Monitoring (DAM) monitors all activity on the database, whether that be a data pull or a login. An essential requirement is for the DAM solution to alert users and admins whenever someone logs in and whenever an anomaly occurs, such as a large data extract.
In that case, however, the unauthorized data access might have already occurred. It is not a preventative measure. Instead, it is a reporting and alert mechanism that informs organizations of unauthorized access.
Mamori’s DAM has built-in preventative features that monitors all connection and SQL activity, with the ability to set policies for connection, statement and data access. Try our DAM solution for free or schedule a demo to see how it works.
PRIVILEGED ACCESS MANAGEMENT (PAM) THAT EXTENDS TO DATABASE
For ransomware to spread, it’ll need more privileged access so they can access and encrypt more critical business data. If the organization implemented a Privileged Access Management (PAM) solution, then the ransomware damage is significantly reduced when it cannot access privileged accounts. Basic protection measures for PAM includes monitoring and recording all privileged sessions and single sign-on (SSO). An important practice when using PAM is implement principle of least privilege – only grant access to parts of the network that are necessary for the employee to do their job.
Mamori’s PAM module does all the above and more. Mamori uses a zero-trust methodology where all access has to be authorized, authenticated, and validated. That means using SSO and 2FA for RDP, SSH, and direct database access, using key-based access, masking data based on privilege, monitoring, least privilege access on-demand (a just-in-time security practice that grants access on an as-needed basis) and more. Try for free or schedule a demo to see how it works.
Image: Mamori M4PAM complements your existing PAM solution by extending controls down into database operations and data
Image: Mamori M4PAM has all the controls required by security and data privacy compliance requirements.
ON-DEMAND WORKFLOW AND POLICIES
When providing access to application and data, IT admins typically provide excess access during account creation to save time. Further, these accounts are usually forgotten because of the excess workload of IT admins. These forgotten, unused accounts (“zombie” accounts) that still have access can be quietly used by a cyber-criminal. Further, having multiple zombie accounts increases the attack surface and chances of cyberattack. The better approach is to automate and simplify this process by using an on-demand approach, where IT admins approve access requests instead of over-provisioning access.
Related: How to Simplify and Automate ISO 27001 Access Controls
DATA MASKING WITH ROW AND COLUMN SECURITY
Row and column security is a data privacy control within the database that masks data within a column or a row. We see this as the asterisk (*) sign that replaces certain numbers or words, commonly seen in masking social security or phone numbers. Data masking with row and column security adds another layer of security to prevent cyber criminals from accessing sensitive data, even when they have access to the database.
2FA ON EVERY RESOURCE ACCESS
2FA and MFA are typically used to secure account access. But many fail to realize that 2FA can be used to add another layer of access security to the database and to certain resources within a database, especially high-value sensitive data. These additional layers of authorization can deter the majority of cyber criminals from fully carrying out an ransomware attack.
Best Practice #5: Being Prepared for Successful Ransomware Attack
Even if you’ve implemented all the best practices listed here, there is still a possibility that ransomware hackers can carry out an attack. Most common scenarios are when a firm is targeted by social engineering, or when an insider opens the door to a ransomware attack. In those cases, below are a few practices that you can use to be prepared.
ENCRYPTION ROLLBACK
This is a tool that detects instead of prevent. This tool monitors file changes within a system, and what program or process was used to change those files. When anomalies occur, such as files being modified, deleted, or encrypted by ransomware, this tool detects and automatically reverse that action. The downside of most of the rollback tools, however, is that it requires access to the organization’s backup files. In other words, if the organization’s backup files are deleted or encrypted, then most of these tools will be rendered useless.
IMMUTABLE BACKUPS
Backup files and snapshots should be immutable. Meaning, the data cannot be overwritten, changed or deleted. This may seem like a saving grace and the best option to fight against ransomware. However, if an organization can successfully restore and recover from backups, then wouldn’t ransomware cybercriminals be out of business by now?
The problem with backups, even those that are immutable, is that the ransomware might attack the entire backup environment or lay hidden inside the backups. Once data is restored, the ransomware can be reactivated immediately if the ransomware is not properly removed. That’s why it is very important that the organization take preventative measures to block ransomware from getting a foothold.
RECOVERING FROM BACKUPS
If the ransomware carried out a successful attack, the only option left is to restore from your backups, assuming they are immutable or if the cybercriminals somehow didn’t encrypt it. The best practice here is as follows:
Turn off and isolate the affected servers. It may be guesswork at this time, but you have to prevent the ransomware from infecting the entire network, if not already. The number one priority is to search for patient zero to begin the cleanup process.
Keep working from your backup files. If you have a backup appliance capable of operating as a production server, keep using it until you are fully recovered. If you have cloud backups capable to fulfill daily operations without delay, use it. It’s important to operate from a backup that you think is clean.
Thoroughly clean your systems and devices. Make sure your entire network and devices are free of malware. Your backup solution should continue to backup the latest work while you clean your systems.
Failback to production. Once systems are cleaned, failback to production with the latest work to resume work as usual.
How Mamori Stops Ransomware Attacks
Mamori prevents ransomware from entering and spreading across your network. Our solution includes Zero Trust Network Access (ZTNA), two factor authentication (2FA), Database Activity Monitoring (DAM), Privileged Access Management (PAM), SQL Firewall, or all of them integrated in ONE solution at a fraction of the cost of traditional solutions.
Our data security approach is proven to stop ransomware. That is why our clients can lower their cybersecurity insurance bill by 40-60% after they implement Mamori.
Not only can Mamori stop ransomware, our solution can also prevent unauthorized personnel from accessing and tampering with your organization’s sensitive data.
Try Mamori for free or schedule a demo to see how it works.